Setting Internet Access Policies
By default, VPN Zones cannot reach Internet applications (![]() ) except the Default Zone which can access the Internet in backhaul (bh) mode (see below). Indeed, Internet access is by default authorized in the LAN, either through the underlay (MPLS) or through the overlay.
) except the Default Zone which can access the Internet in backhaul (bh) mode (see below). Indeed, Internet access is by default authorized in the LAN, either through the underlay (MPLS) or through the overlay.
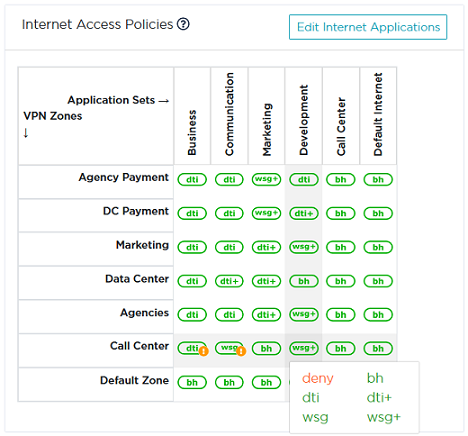
To change the default status, click the icon for each VPN Zone/Application Set pair in the Internet Access Policies matrix and select one option among bh, dti, dti+, wsg and wsg+ and deny. This configuration is kept after any SD-WAN Orchestrator upgrade.
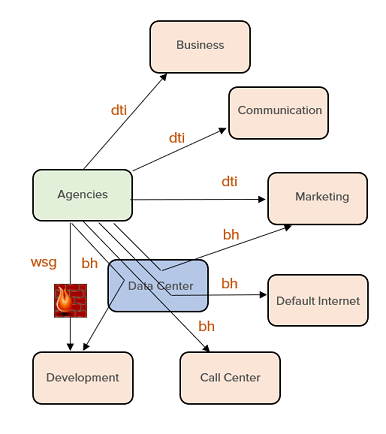
The following diagram illustrates the Internet Access Policies that have been defined for the Agencies VPN zone to access the applications in the Business, Communication, Marketing, Development, Call Center and Default Internet application sets ("Use Case 11").
|
deny |
The traffic is dropped. |
||||||
|
bh |
Backhaul: the traffic is routed to the Data Center ip|engine (through underlay or overlay according to the current deployment) which must be able to route it to a firewall or proxy.
Backhauling can be activated on hub ip|engines (in Router or Bridge-Router mode) and on ip|engines in Bridge mode. |
||||||
|
dti |
Direct to Internet: the traffic is directly sent to the Internet. This policy is only available for Internet interfaces. With an interface which is not eligible for DTI (for example, MPLS interface), the traffic is dropped. You may activate eligibility to DTI globally in Advanced Configuration -> Transport Network Settings or individually on any Internet L3 interface. As a consequence, NAT is automatically enabled since DTI traffic must be NATted by the WAN interface. Also, Local Port Forwarding parameters may be specified for this interface. |
||||||
|
dti+ |
Direct to Internet or Backhauling: the traffic is either sent in DTI if the interface authorizes it (Internet interface), or backhauled to the Data Center (for a MPLS interface). To activate this policy, refer to the bh and dti options. |
||||||
|
wsg |
EdgeSentry or Web Security Gateway: the traffic is routed via an IPsec tunnel to EdgeSentry or to a web security gateway in the Cloud. This policy is only available with Internet interfaces when EdgeSentry is activated or when there is a configured Web Security Gateway. The traffic is dropped on an interface if either EdgeSentry is not activated on it or this interface is not eligible for WSG (there is no configured WSG tunnel). |
||||||
|
wsg+ |
EdgeSentry or Web Security Gateway or Backhauling: the traffic is either routed to EdgeSentry (with an interface where EdgeSentry is activated) or to a web security gateway (with an interface eligible for WSG), or the traffic is backhauled to the Data Center (EdgeSentry is not activated and there is no configured WSG tunnel). To activate this policy, refer to the wsg and bh options. |
Policy Behavior by Interface type and configuration
|
Interface/Policy |
dti |
dti+ |
wsg |
wsg+ |
bh |
deny |
|---|---|---|---|---|---|---|
|
L2 |
drop |
allow |
drop |
allow |
allow |
drop |
|
L2 + eligible DTI |
not available |
|
|
|
|
|
|
L3 |
drop |
tunnel to dc |
drop |
tunnel to dc |
tunnel to dc |
drop |
|
L3 + eligible DTI |
dti |
dti |
drop |
tunnel to dc |
tunnel to dc |
drop |
|
L3 + WSG |
drop |
tunnel to dc |
tunnel to gateway |
tunnel to gateway |
tunnel to dc |
drop |
|
L3 + DTI + WSG |
dti |
dti |
tunnel to gateway |
tunnel to gateway |
tunnel to dc |
drop |
Impact on the Network Services
If at least one ip|engine within the VPN Zone has no WAN interface that supports 'dti', a yellow exclamation mark is displayed on the Internet Access Policy icon:  . When positioning your cursor over the exclamation mark, you may know which ip|engine(s) are involved. The same information is displayed at the top of the Network -> Zone-Based Firewall main window.
. When positioning your cursor over the exclamation mark, you may know which ip|engine(s) are involved. The same information is displayed at the top of the Network -> Zone-Based Firewall main window.
The same rule applies to 'wsg'.
In these error cases, the traffic is dropped and all the SD-WAN Orchestrator services are deactivated.